Password Spraying: How hackers compromise your email server

A threat worth understanding
Email administrators are constantly dealing with the looming threat of authentication attacks. When an account has been compromised, it can be used for phishing, spam, malware distribution, and other illegal activity. If you’re running an email server, this could have many implications — including getting blacklisted. One of the most common authentication attacks is the password spraying attack. By understanding what password spraying is and how it works, you can defend your server more effectively.
What is password spraying?
Password spraying is a type of authentication attack where hackers select a few passwords to try against millions of accounts. It’s an effective way to bypass rate limiting measures, where a limit is placed on how many times you can attempt a password within a certain time frame. For email platforms, rate limiters are pretty much essential as a security measure.
“Dutch security researcher Victor Gevers managed to hack Donald Trump’s Twitter with passwords “yourefired” in 2016 and “maga2020!” in 2020.” 1
Though it’s inadvisable, people still like their easy passwords. Whether it’s their cat’s name or their birth year, people are drawn to passwords they remember. They also like recycling them and using those same passwords everywhere. This is one of the reasons password spraying attacks, which have been around since the mid-2000s, still get so much attention today.
Password spraying vs brute force attacks
Password spraying is the inverse method of another authentication attack, the brute force attack. A brute force attack is when a threat actor attempts many passwords against one targeted account.

Brute force attacks are rarely used in network attacks anymore because they trigger rate limiters. This attack tactic is more often used in data breaches, where even encrypted passwords can be broken in mere minutes locally.
Password spraying attacks involve fewer password attempts per account, meaning rate limiting can be circumvented. Factor in the other tools at a hacker’s disposal, including botnets and infected devices, and the number of passwords that can be tried on an account without triggering rate limiting goes up exponentially.
Password spraying vs dictionary attacks
A dictionary attack is any authentication attack that uses a “dictionary.” A dictionary can be any data set or list, not just words from an actual dictionary. For instance, a dictionary could be a list of names and passwords from a previous data breach, or a data set some hacker is selling on the dark web.
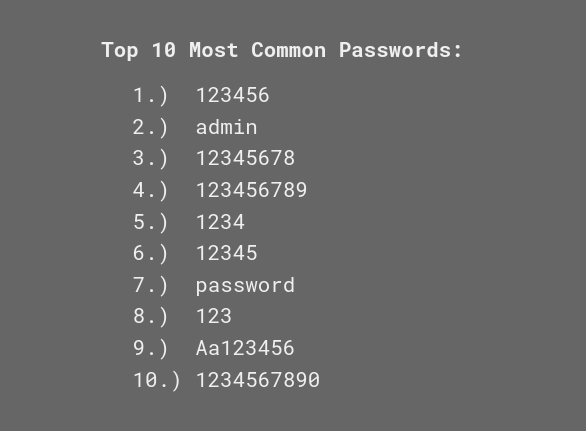
Experienced hackers know that people like using the same passwords again and again. As such, dictionary attacks can be quite effective as part of password sprays and brute force attacks. Once people’s credentials enter a dictionary, hackers will start looking for other places the same credentials will work.
How do hackers find your username or email?
When hackers conduct password spraying attacks, they attack a massive amount of users at the same time. These targeted email addresses and usernames are often found in previous data breaches or acquired via the dark web, as well as through dictionary attacks using automated tools.

Threat actors also use web scraping tools to obtain email and username data from public sources on the web like social media and websites. If none of those work, they also commonly employ social engineering techniques like email phishing and impersonation to extract information from unsuspecting individuals. This is most commonly done if there’s at least one compromised email that can be used to phish others in that organization.
How to stop a password spraying attack
Stronger passwords
The first thing you can do to guard against password spraying is to enforce a better password policy. Strong, complex passwords are your first line of defense against authentication attacks. Emphasize the importance of passwords that are (a.) not dictionary words, and (b.) contain a sizable combination of upper and lowercase letters, symbols, and numbers.
Multi-Factor Authentication (MFA)
Wherever possible, implement Multi-Factor Authentication (MFA). If you used your dog’s name as your password and a hacker cracked it, Multi-Factor Authentication would add an extra layer of protection against unauthorized access. This could mean sending a one-time password to your mobile device, or the need for your fingerprint or another biometric.

Multi-Factor Authentication measures often include one-time passwords and biometrics.
Unique passwords
In general, you should use different passwords for all of your accounts. Reusing the same password might seem convenient, but you’re putting your data and privacy at risk. If a hacker gets the password right for one of your accounts, they will inevitably try it against your other accounts. As a rule of thumb, never use the same password for different accounts.
Unique usernames
Having an uncommon username that hasn’t been found in a data breach is a fantastic way to mitigate password spray attacks. If you don’t show up in the attacker’s target list, they cannot try a password spray attack on you. Refrain from using dictionary words for your username, and try to make it unique. Generally, try to use different usernames for different platforms and accounts.
“With the number of unique phishing attacks reaching 5 million, 2023 was the worst year for phishing on record.” 2

Footnotes:
1. Courtesy of HUIB MODDERKOLK, DE VOLKSKRANT
2. Courtesy of APWG.ORG
