How to Prevent Spoofed Emails on cPanel Email Servers (Part 1)

Keeping email users safe from threat actors is one of the most critical hosting challenges for businesses. Threat actors use a variety of threat techniques to deceive and harm victims, including Email Spoofing to create Spoofed Emails which is one of the most common but effective email threats.
This two-part article will focus on Spam Filtering Best Practices to reduce the amount of Spoofed Emails entering mailboxes hosted on cPanel — one of the most widely used web hosting control panels in the World. In the first part, we will learn about the characteristics of Spoofed Emails and the ways threat actors use them to deceive victims. Then in the second part, we will learn about the different methods to prevent Spoofed Emails.
Read on to learn more about Spoofed Emails.
What are Spoofed Emails?
Spoofed Emails are a type of email threat where threat actors send emails that have been manipulated with forged information to seem as if it originated from a trusted source. By presenting themselves as a trusted authority figure, this email threat circumvents your natural skepticism leaving you more vulnerable against deception. Imagine someone wearing a fancy white doctor coat and someone wearing socks with flip-flops asking you to buy medicine — one is definitely more convincing than the other.
Spoofed Emails use forged sender information of trusted entities to circumvent your natural skepticism leaving you more vulnerable against deception.
Threat actors combine other threat techniques alongside email spoofing to deceive you into doing something that you would otherwise not have done such as:
- Send wire payments to fraudulent bank accounts.
- Input credentials into fake websites.
- Reveal sensitive information.
- Execute malicious attachments.
Businesses without a comprehensive protection strategy against Spoofed Emails are at a higher risk of financial damage. Just look at the most recent FBI Internet Crime Report where spoofing was directly responsible for $669,162,215 USD of global damages between 2018 and 2021. Not to mention the risk of reputation damage which can be absolutely devastating to a business.
How Email Spoofing Works?
There are two main pieces of sender information that threat actors can forge within email: the (1) MAIL FROM and (2) From Header.
Spoofed MAIL FROM
The MAIL FROM is a command used to identify the sender of the email as part of the Simple Mail Transfer Protocol (SMTP). Compared to physical letters, the MAIL FROM can be thought as the Return Address on the envelope which is the reason that this address is also known as the Envelope From address and has an equivalent email header called the
Return-Path header.

The sender information in the MAIL FROM is not immediately viewable from the email client, so threat actors rarely forge this information to deceive email users. Instead threat actors may forge this information in order to exploit whitelists and avoid spam filters. After all, it’s not entirely uncommon for businesses to whitelist the sender address of their close partners.
Spoofed From Header
The From Header is an email header used to identify the sender of the email body and consists of the From Name and From Address. Compared to physical letters, the From Header can be thought as the sign-off at the bottom of the letter.
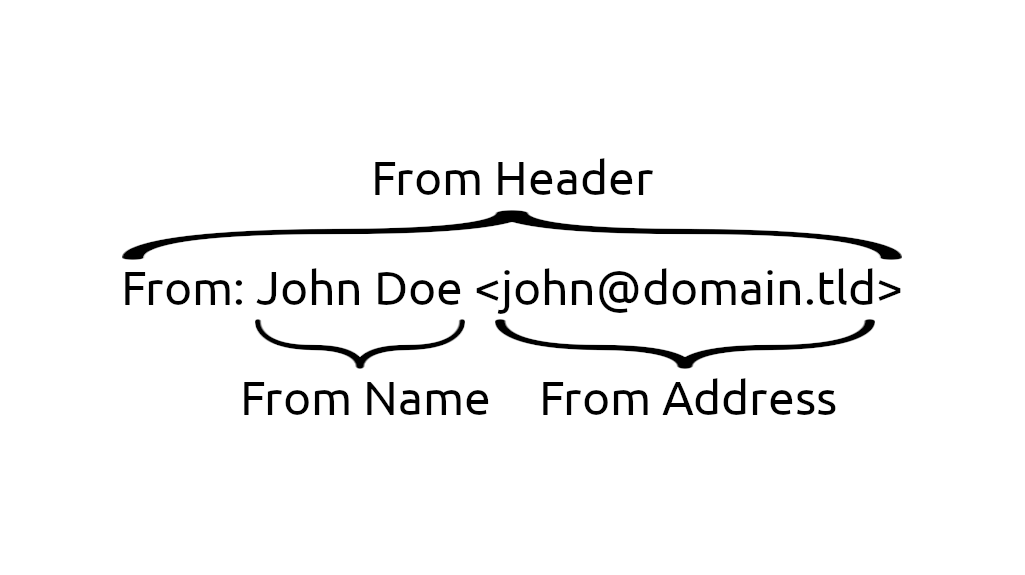
The sender information in the From Header is immediately viewable from the email client, so threat actors frequently forge this information to deceive email users. It’s typical for threat actors to forge the information of well-known public entities like governments, banks, and businesses (even your own) that anyone in the World is likely to know and engage with on a regular basis.
There is no rule that the sender information in the MAIL FROM and From Header need to be an exact match. In general, the sender local-part (john) not matching in the MAIL FROM and FROM Address is not too concerning but the sender domain (domain.tld) should usually be the same.
However, there are legitimate cases for when the sender domain do not match. It’s not uncommon for an Email Service Provider (ESP) to send emails on the behalf of their customers. In this case, the MAIL FROM contains the ESP sender information while the From Header contains their customer sender information. Some examples of ESPs would be SendGrid and Amazon AWS.
Spoofed Emails as seen from the Email Client
Part of the reason for the effectiveness of spoofed emails is the default message display behavior of email clients. Certain sender information is shown immediately to you, while other sender information requires more effort to view. Threat actors take advantage of this by prioritizing spoofed sender information that is immediately viewable.
Let’s look at an example of a spoofed email as seen through the default Roundcube Webmail Client on cPanel. This particular spoofed email forges PayPal sender information in order to deceive recipients to input their credentials into a fake website.
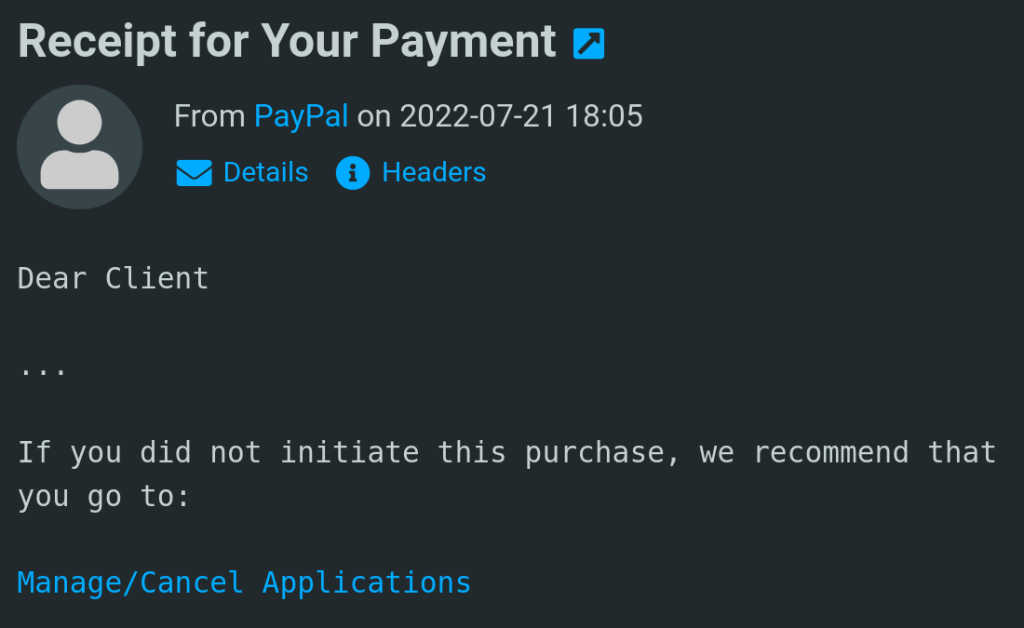
Notice how the PayPal company name is immediately viewable — that is the spoofed From Name of the From Header. Threat actors can be very successful especially when the spoofed company is one that the recipient deals with on a regular basis.
Recipients on the lookout against spoofed emails will want to look at the next most immediately viewable sender information — the From Address of the From Header. By comparing the sender information in the From Name and From Address, alarms should be raised when there is a mismatch.
By default with the Roundcube Webmail Client, recipients have to hover their mouse over the From Name in order to view the From Address. Note that the Roundcube Display Messages Preferences can be configured to display both the From Name and From Address simultaneously.
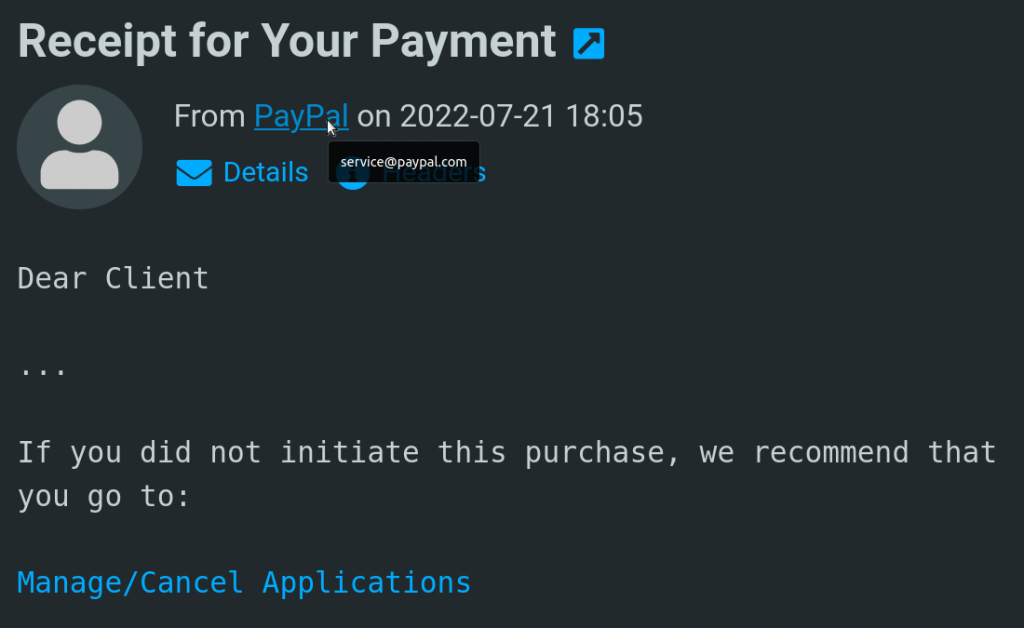
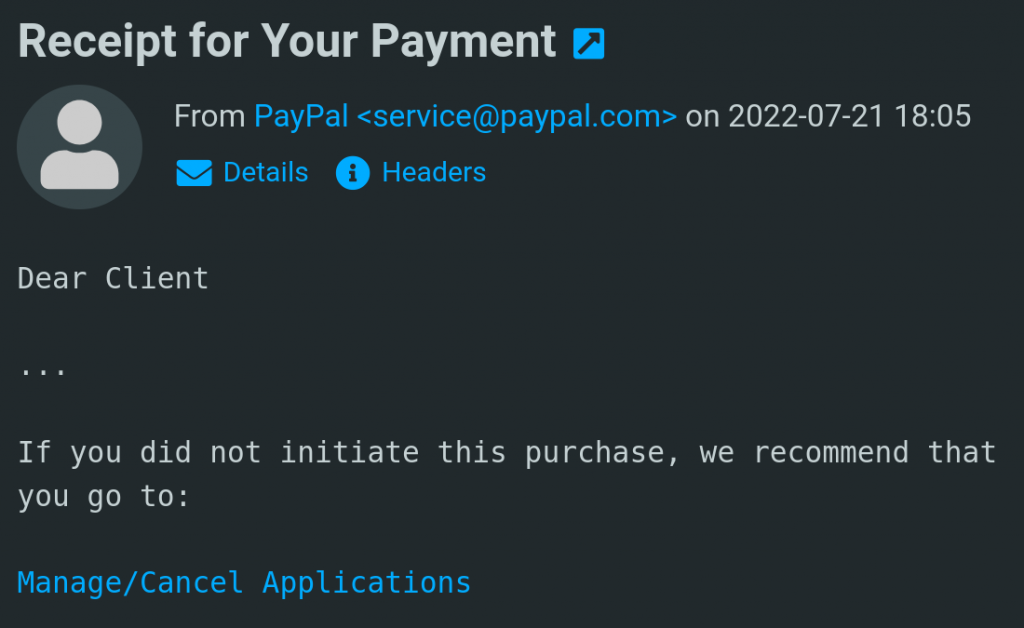
In this case, the threat actor also spoofed the From Address with an official PayPal address. Just based on this information, recipients may not be able to identify whether this is a spoofed email.
The most informed recipients worried about spoofed emails will then want to look at the sender information in the MAIL FROM. In this case with PayPal, a mismatch between the sender domain (paypal.com) in the MAIL FROM and From Header is one of the final lines of defense against spoofed emails.
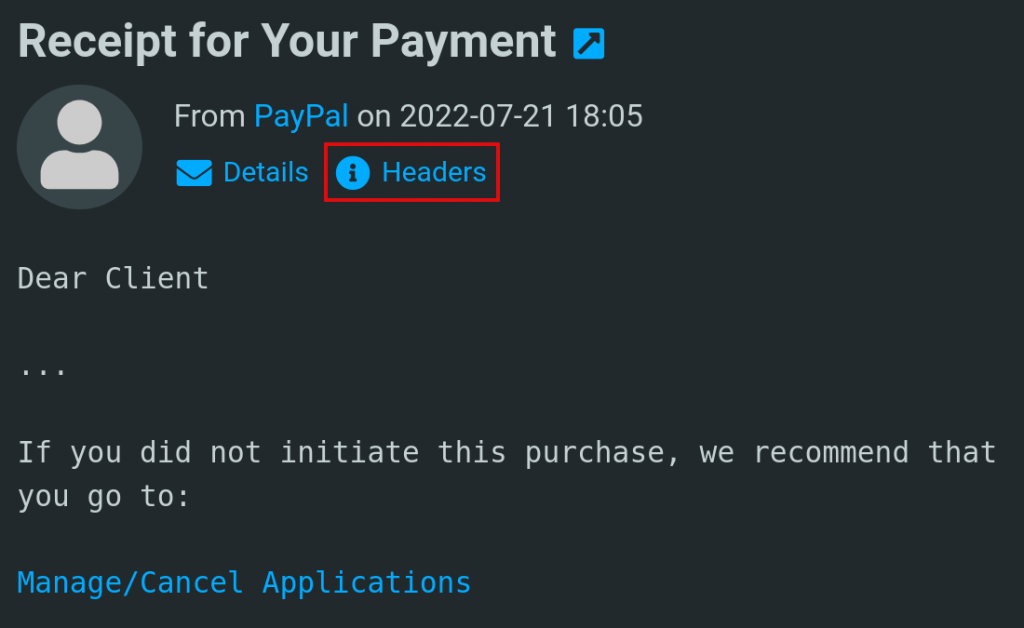
Fortunately the Roundcube Webmail Client makes it easy to view this information only requiring a single click of the “Headers” button. It typically takes more steps with other email clients requiring that you open the “More Action” menu and click on the “View Source” button.
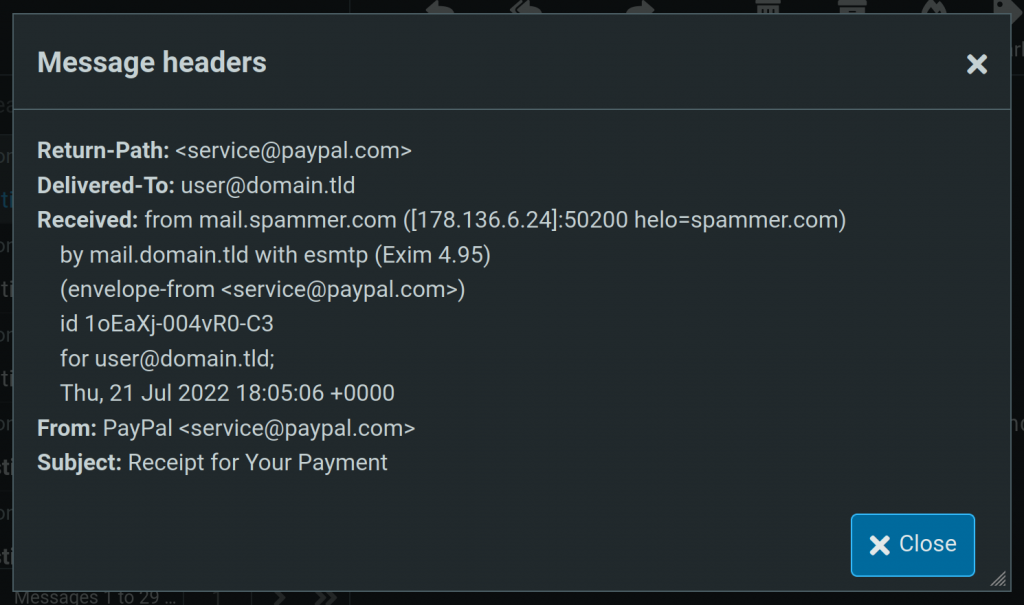
Don’t forget that the Return-Path header is equivalent to the MAIL FROM. Once again, the threat actor spoofed the sender information in the MAIL FROM with an official PayPal address. At this point, the recipient has looked at all the typical places for spoofed sender information but nothing stands out as being suspicious. It looks like a PayPal email sent by PayPal themselves.
However, the more astute of recipients will notice the Received header and how the hostname associated with the connecting email server does not appear to be from PayPal. AHA — finally an indicator that this email isn’t what it seems to be.
Conclusion
While the ability for recipients to identify spoofed emails themselves is valuable, it should not be the preferred method. For one, the identification process can be error prone especially when trying to read and understand the email headers. Another drawback is that this process takes a lot of unnecessary effort — time spent on this should have been spent on other more valuable tasks.
As responsible email administrators, we need to demand better solutions and rely more on technology rather than human behavior to identify spoofed emails. Hence, it’s better to stop spoofed email from even getting delivered in the first place — less errors, less effort, and ultimately less risk.
Check out the second part of this article to see how we can prevent spoofed emails with cPanel built-in protection.
